In recent months, we’ve seen a dramatic rise in phishing attempts targeting hosting company customers. The pattern is simple: someone impersonates a known brand and sends a fake email urging the recipient to urgently renew a domain or hosting service. Everything looks very professional — logos, formatting, and even links that lead to websites nearly identical to the originals.
This phenomenon has reached a massive, even global scale. Cybercriminals don’t limit themselves to one market or language — they attack users all over the world using the same tactics: spark panic, impersonate a trusted brand, and force the recipient to act quickly.
Fighting this threat has become a daily task for hosting companies across continents. These warnings have been issued by, among others:
- HOSTAFRICA – warning customers in Africa and Europe.
- WHC.ca – documenting frequent scams in Canada.
- IONOS – an international provider warning users in multiple languages.
- Namecheap – a U.S.-based provider reminding users about the issue every few months.
All of them emphasize the same thing: phishing knows no borders. Fake websites impersonating hosting providers appear every day. They’re often active for only a few hours — just long enough to scam hundreds of people and vanish without a trace.
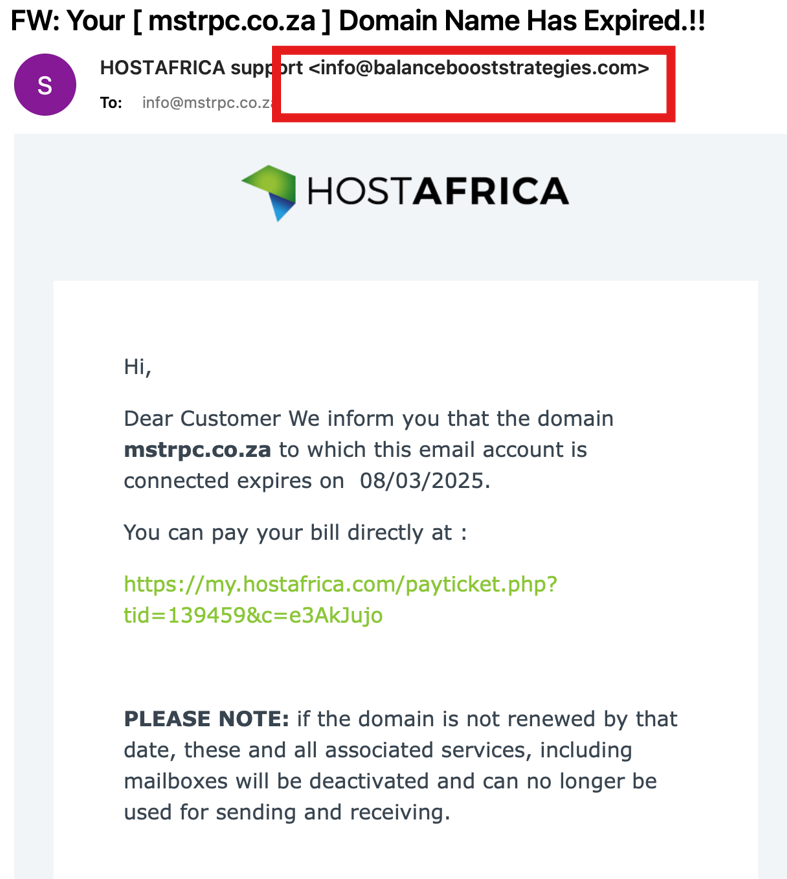
What does a typical phishing attack look like?
Domain renewal phishing has several common traits that make it especially effective — and dangerous.
Email subject: urgent and anxiety-inducing — “Renew Your Domain [domain name]”, “Hosting Expiry Notice”, “Final Notice: Renew Now”. Often includes specific dates to increase pressure.
Sender: pretends to be a known company (e.g., [email protected]), and the message itself is formatted nearly identically to official provider emails.
Content: looks credible, sometimes includes real WHOIS data — domain expiry date, company name, even contact details. This makes the user believe it’s legitimate.
Link: leads to a fake payment page, often secured with an SSL certificate (!), but using a completely unrelated domain — e.g., renew-domain-secure.com, crafted to look trustworthy.
Real-life example? Meet John Smith, owner of a small electronics webshop. One day, he received an email saying his domain js-techstore.com would expire in 48 hours. The sender appeared to be a familiar registrar, with correct WHOIS data. Busy fulfilling orders, John clicked the link, paid for the “renewal,” and… unknowingly gave his card details to scammers. Within an hour, his bank account was drained, and access to his site was blocked — the phishing page had also captured his hosting panel login.
These attacks work because they prey on stress, routine, and lack of time. John wasn’t naïve — he just acted too fast. And that’s exactly what scammers count on.
Why this isn’t a data breach
One of the most common customer questions: “How did they get my domain and info? Does this mean my hosting provider was hacked?”
The answer is: most often, no.
The data used in these attacks usually comes from public sources — mainly WHOIS registries, which are publicly accessible for many domain extensions. With TLDs like .pl, .com, .net, or .org, domain owner details (whether individual or business) are often public or accessible via paid or free registrar APIs.
Cybercriminals use automated tools to collect such information en masse. Bots scan WHOIS for domains nearing expiration and generate personalized phishing emails at scale. The more realistic the message — with the domain name, expiration date, and even registrant details — the higher the chance the recipient will click.
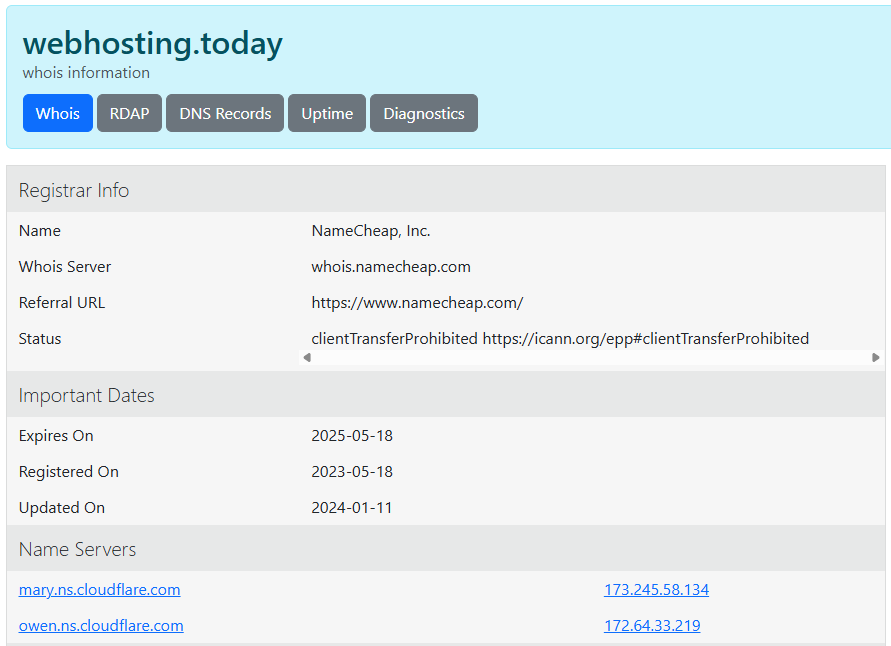
Even if WHOIS data is hidden (e.g., via “Privacy Protection”), that doesn’t guarantee safety. Attacks still occur, though less personalized — using generic messages like “Your domain expires tomorrow – renew now!”. These may be less effective individually, but volume makes up for it.
There’s no need for a data breach at your hosting provider to receive such a message. It’s simply the result of mass scraping of publicly available data.
What hosting providers can do
- Warn your customers – regularly, not just in blog posts. Ideally: banners in the dashboard, quarterly emails, social media posts.
- Share independent resources – that’s why this article exists. If you want to warn your customers, you can link here. There’s no branding or competing offers — it’s a pure guide.
- Implement SPF/DKIM/DMARC – proper email configuration reduces the risk of spoofing (though it won’t eliminate it entirely).
- Report fake domains – to registrars and to Google Safe Browsing.
- Educate – influence the awareness of your customers through social media, a company blog, and guides.
What users can do
Always check the sender’s email address – not just the display name (e.g., “Customer Support”), but the actual email. Scammers often use lookalike domains, e.g., [email protected] instead of [email protected]. The difference may be subtle but critical. If in doubt, examine the full email headers — these reveal the actual sending server and routing path. A powerful tool for spotting impersonation.
Don’t click links in emails – even if they look legitimate. Instead, open a new tab and type the hosting provider’s address manually. Clicking the link may take you to a convincing fake that steals your credentials or money. Never download attachments from suspicious emails — they can carry malware that hijacks your device or steals banking and email credentials.
Report suspicious emails – every company being impersonated should be made aware. Your report helps them respond faster, warn others, and shut down fake sites. In Poland, you can also contact CERT Polska (incydent.cert.pl).
Only make payments through your hosting provider’s official dashboard – never via email links. If you’re asked to pay via an email link, pause and verify it at the source. Better safe than sorry.
Enable two-factor authentication (2FA) – on every account that supports it. Not just your hosting panel, but also email, banking, social media, and cloud services. Even if a hacker has your password, the additional code from an app or SMS can stop them cold.
Failure to follow these steps is the most common reason for infected devices, stolen credentials, compromised email accounts, and ultimately — user data breaches. Phishing combined with carelessness is the most effective weapon in a hacker’s arsenal.
Understand this: a data breach is only the beginning. In the worst-case scenario, attackers can gain access not just to one service, but to entire email accounts — often hosted elsewhere. That opens the door to the rest of your digital life: social media, selling platforms, cloud accounts, even banking.
And if your email is tied to your domain registrar account? Then you’re looking at the most dangerous outcome — domain theft and unauthorized transfer. A digital smash-and-grab: fast, silent, often irreversible.
That’s why 2FA is not a luxury or gimmick. It’s a gatekeeper that, in a critical moment, can save your data, your reputation — even your business.
Together, let’s build security in the net
This isn’t the end of phishing attacks. On the contrary — it’s only the beginning of a much bigger problem. Every year, more users register domains, launch online stores, blogs, or business websites. These people are ideal targets — often inexperienced, unaware of the risks, and trusting of anything that looks professional.
For cybercriminals, it’s a gold rush. The more targets, the greater the scale. Every success fuels more malware, more botnets. Every clicked link, every downloaded file — is like opening the door to someone’s digital life.
That’s why we need to talk about this openly. Not with fear, but with clarity. If we don’t act together — as an industry, as providers, and as users — the number of victims will only grow month after month. Education and sharing real-world examples is no longer optional. It’s necessary.
If you run a hosting company and want to help raise awareness — link to this article. You can also send us your own examples (contact(at)webhosting.today) — we’ll keep this post updated.
Together, we can limit the damage caused by these campaigns.
