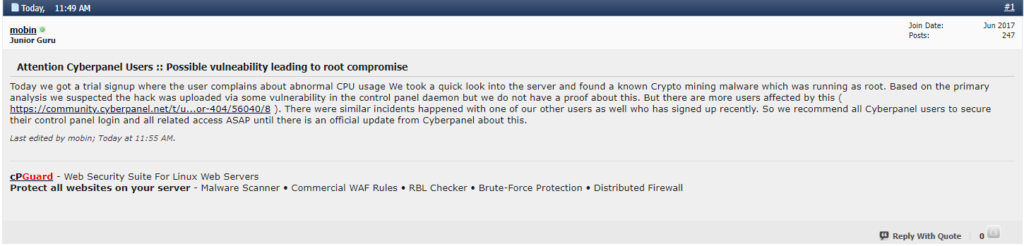
Today, on the pages of WebHostingTalk.com, a user reported a troubling issue with CyberPanel, drawing immediate attention from the community. The user, “mobin,” shared details of an unusual CPU spike on their server, which, upon investigation, turned out to be the result of crypto-mining malware running with root-level permissions. “We found a known crypto mining malware running as root… suspected to have been uploaded via a vulnerability in the control panel daemon,” mobin explained. This revelation quickly sparked a discussion among other CyberPanel users, worried about similar vulnerabilities.
The issue caught the eye of security researcher DreyAnd, who posted an analysis on their cybersecurity blog. DreyAnd identified this as a 0-day vulnerability, meaning it was a previously unknown flaw that allowed attackers to execute remote code without needing any authentication. This “pre-auth RCE with root privileges,” as DreyAnd described it, effectively enabled attackers to take full control over affected systems. This serious vulnerability, especially alarming for users managing business-critical applications, highlighted significant risks within the CyberPanel environment.
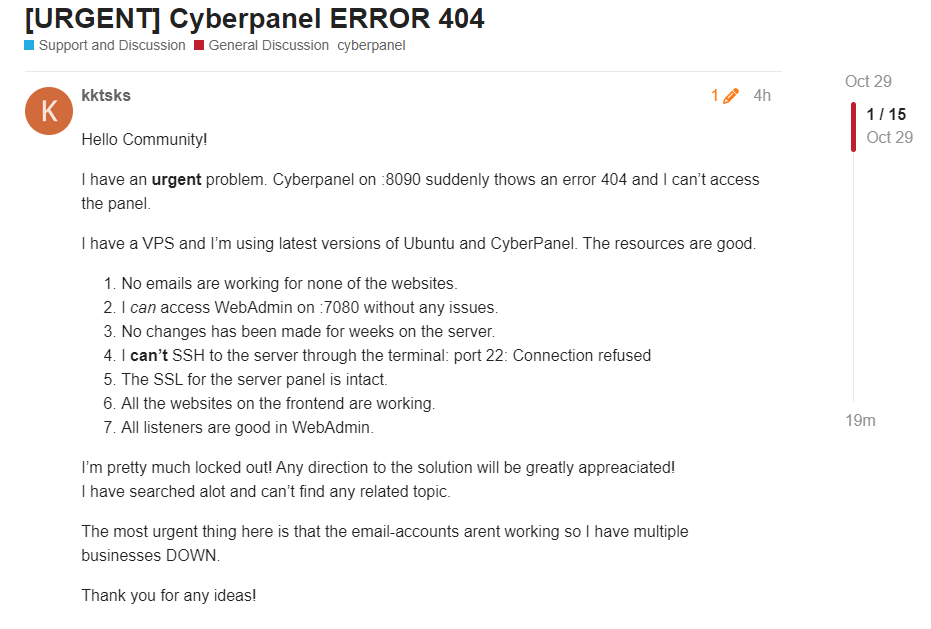
Soon after, discussions on CyberPanel’s official forum revealed that other users had encountered similar issues. Reports of blocked access, persistent 404 errors, and downtime for websites hosted on CyberPanel began to surface. Users noted significant CPU usage spikes and a process identified as ‘/var/tmp/kdevtmpfsi,’ linked to the malware. A user named “kktsks” described finding their servers crippled:
Responding to the reports, CyberPanel released an official statement confirming the vulnerability. They acknowledged the oversight and explained that a patch had been released within 30 minutes of verifying the issue, although they initially refrained from publicizing it to prevent attackers from exploiting unpatched systems. “We released a security patch within 30 minutes after verification,” CyberPanel assured, encouraging all users to apply the update immediately.
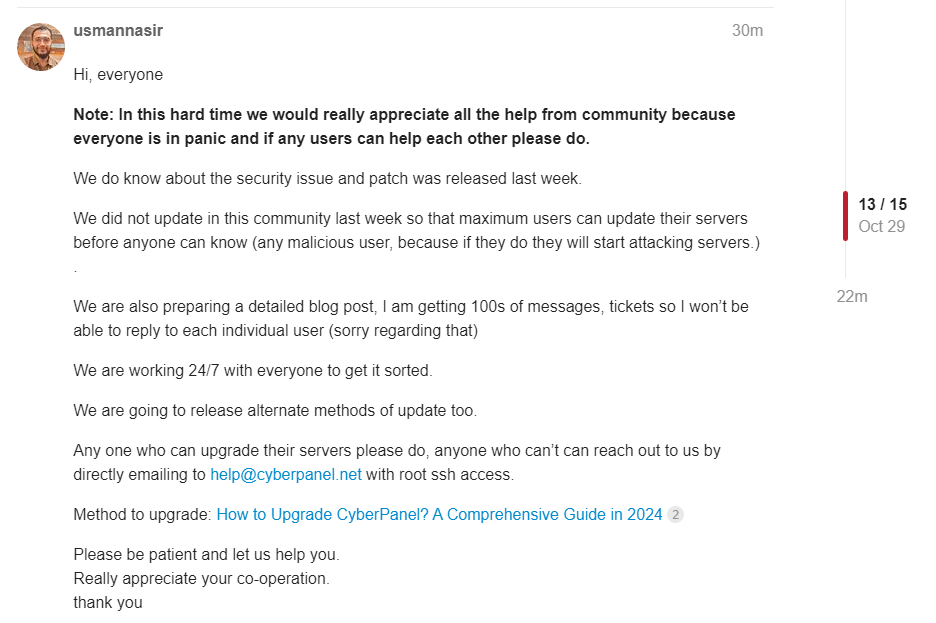
For those unable to update due to restricted SSH access, CyberPanel provided instructions and offered direct support.
CyberPanel’s advice to all users is clear: update the software without delay to ensure protection against this vulnerability. This incident underscores the critical importance of timely security updates and transparent communication, especially when security is at risk. With the patch now available, CyberPanel’s community is focused on securing their systems, while developers are working to enhance communication and support to help users navigate disruptions more smoothly.
Kamil Kołosowski
Author of this post.
